Introduction
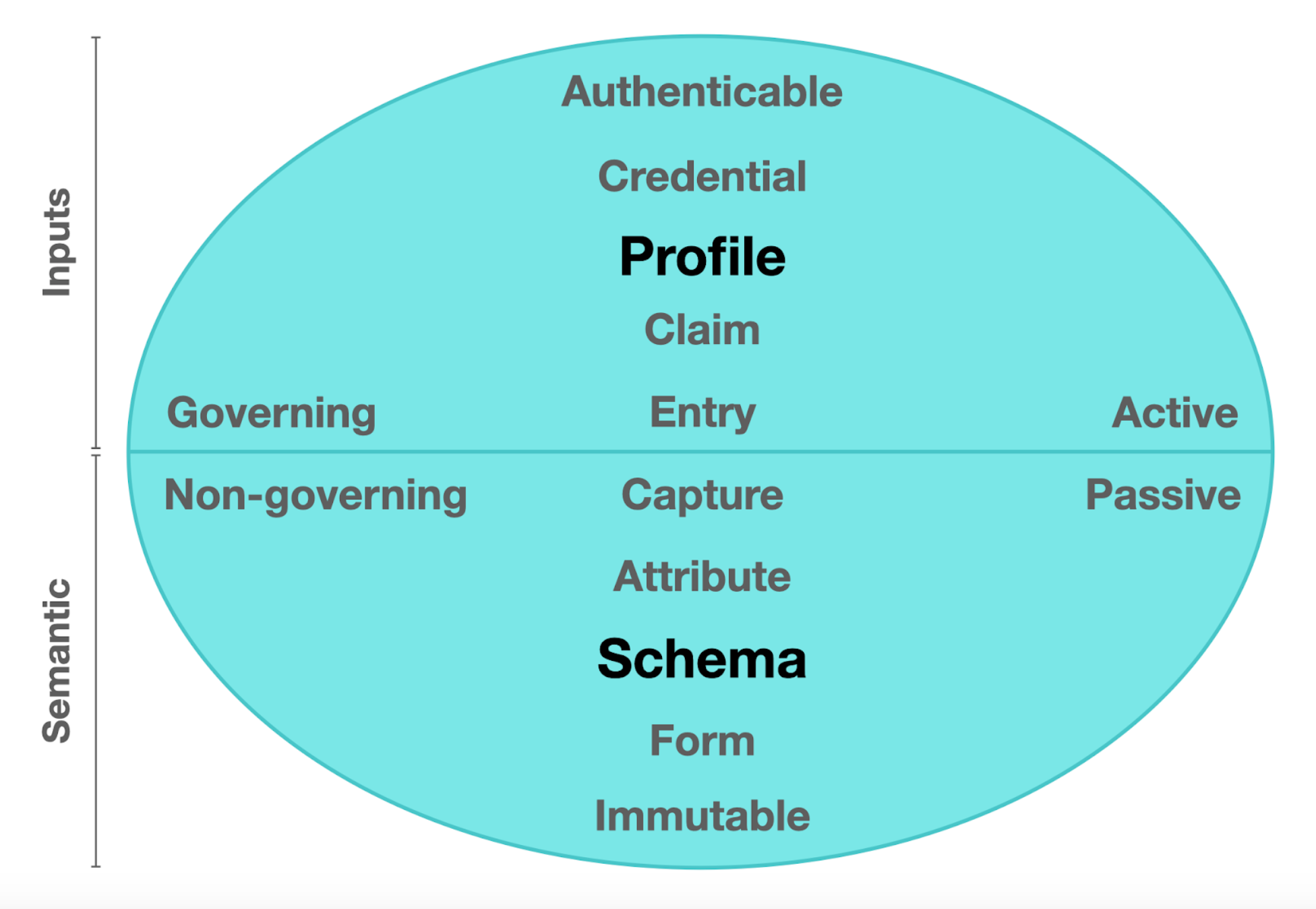
The Inputs and Semantics Working Group (ISWG) supports a practical approach to further enable the adoption of the Trust over IP dual-stack architecture by bringing a balanced view of decentralized network paradigms to the overall mission of Internet-scale digital trust. All data inputs operated on by any process or system should be authenticable with the semantics providing meaning and context at the time of capture.
Figure 1. Model of Identifier States: A component diagram showing the inputs and semantic counterparts of a balanced network model
Mission and Scope
The mission of the ISWG is to define a decentralized key management infrastructure (Inputs domain) and data capture architecture (Semantic domain) for Internet-scale deployment. The scope of the ISWG is to define specifications and best practices that bring cohesion to data entry (aka Inputs) and data capture (aka Semantic) processes and standards throughout the ToIP stack whether these standards are hosted at the Linux Foundation or external to it. Other working group activities will include creating template Requests for Proposal (RFPs) and additional guidance to utility and service providers regarding implementations in that capacity. This WG will be divided into Inputs and Semantic domain groups and may also organise Task Forces and Focus Groups to escalate the development of certain components if deemed appropriate by the majority of the WG members and in line with the overall mission of the ToIP Foundation.
Meetings
Schedule:
- Inputs Group
US/EU: TBC
- Semantics Group
US/EU: The ISWG meets weekly on a Tuesday from 09:00-10:00 PT / 17:00-18:00 UTC
How to join
You can join the ISWG by signing up for the Foundation mailing list at lists.trustoverip.org. Our mailing list is inputs-and-semantics-wg@lists.trustoverip.org
Members as well as observers are welcome (with the important caveat below).
Participation
For the protection of all Members, participation in working groups, meetings and events is limited to members, including their employees, of the Trust over IP Foundation who have signed the membership documents and thus agreed to the intellectual property rules governing participation. If you or your employer are not a member, we ask that you not participate in meetings by verbal contribution or otherwise take any action beyond observing.
Inputs Group
Inputs domain [active] / what is put in, taken in, or operated on by any process or system
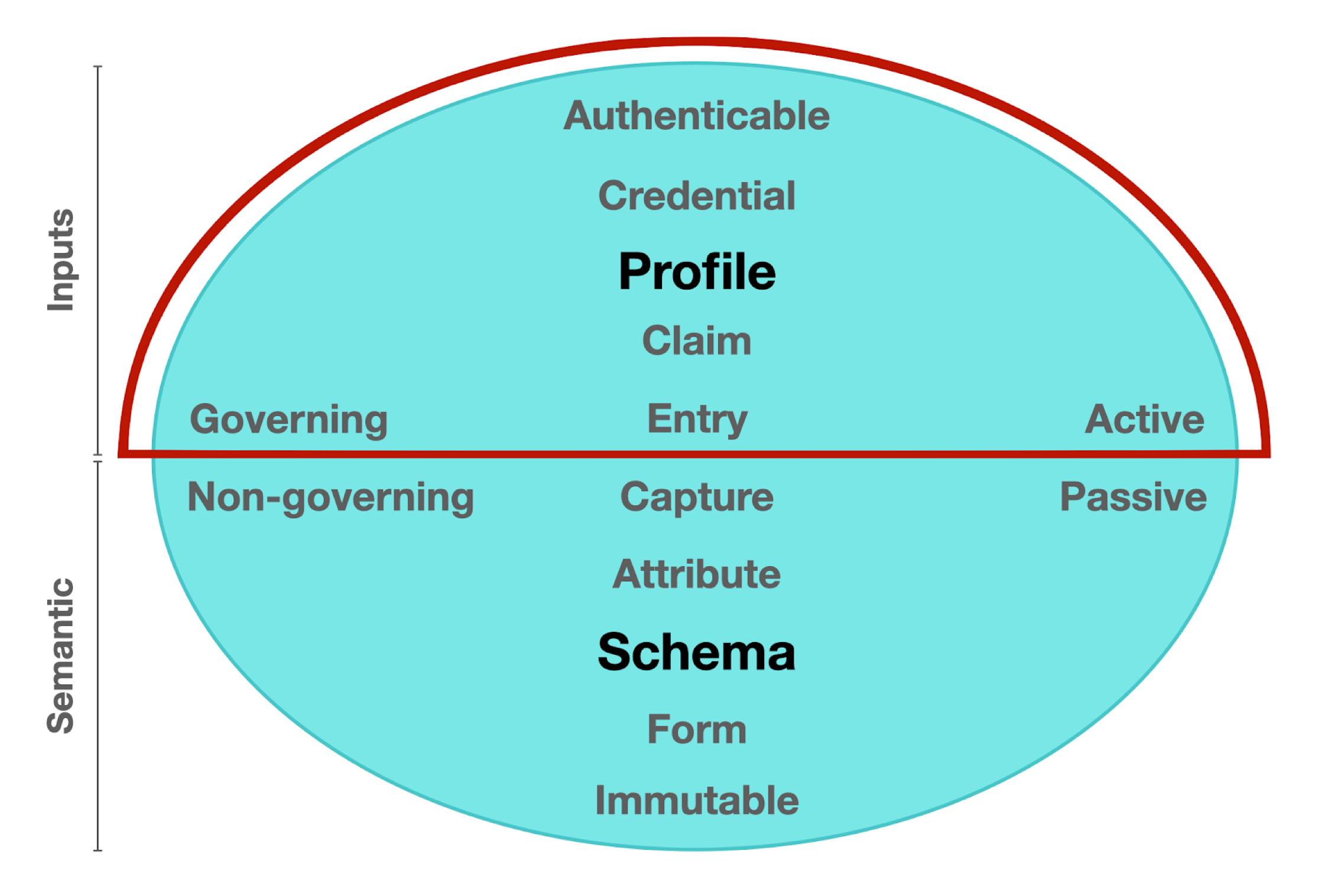
Figure 2. A component diagram highlighting the Inputs domain within a balanced network model.
Data entry is defined as the process of inputting data into a computer using devices such as a keyboard, scanner, disk, sensor, or voice. In a decentralized network, data entry requires a signing key in order to establish that inputted data has come from an authenticable source. In the above component diagram, all elements and characteristics of data entry are depicted in the northern hemispherical Inputs domain.
Mission and Scope of the Inputs Group
The mission of the Inputs group (ISWG-I) is to define a decentralized key management infrastructure that provides self-certifying identifier issuance underpinned by cryptographic one-way functions for Internet-scale deployment. The scope of this sub-group is to define specifications and best practices that bring cohesion to data entry processes and other Inputs standards throughout the ToIP stack, whether these standards are hosted at the Linux Foundation or external to it. Other sub-group activities will include creating template Requests for Proposal (RFPs) and additional guidance to utility and service providers regarding implementations in this domain. This sub-group may also organise Task Forces and Focus Groups to escalate the development of certain components if deemed appropriate by the majority of the sub-group members and in line with the overall mission of the ToIP Foundation.
Chairs / Leads of the Inputs Group
- Chair: Robert Mitwicki
- Vice-Chair: Samuel Smith
Core Inputs Concepts
Key management refers to the management of cryptographic keys in a cryptosystem. This includes dealing with the generation, exchange, storage, use, crypto-shredding (destruction) and replacement of keys. It includes cryptographic protocol design, key servers, user procedures, and other relevant protocols.
Successful key management is critical to the security of a cryptosystem. Developing and deploying the right key management infrastructure will ensure the highest level of security to enable tamper-resistant interactions between governing entities as autonomous peers in a digital system.
Key Event Receipt Infrastructure (KERI)
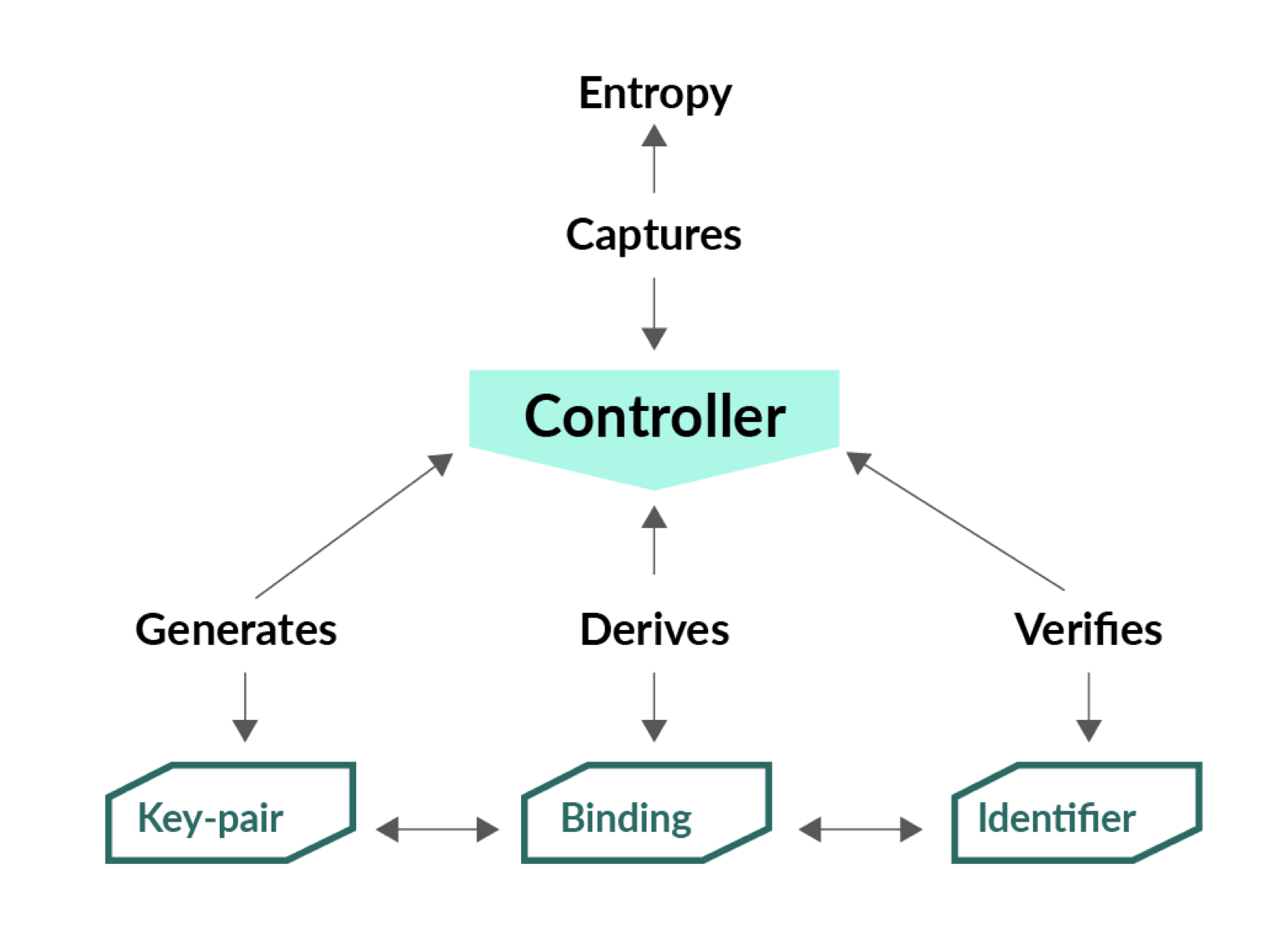
KERI is an architecture that offers information uniqueness from captured entropy by compiling the history of all uses or changes to the public/private key pair. This is achieved by universal self-certifying proofs of the binding between the self-certifying identifier (SCID) and the associated public/private key pairs. It is a truly decentralized key management solution offering the strongest possible levels of pseudonymity, ledger-less identity and separable identifier trust bases for all network participants.
KERI is a secure overlay for an identity system where any digital representation of a governing entity can serve as an autonomous self-certifying root-of-trust. It is a solution that offers secure data control established via self-certifying pseudonymous identifiers. As a standardized global solution for data entry, KERI facilitates sapored data supply chains, enabling a record trail that accounts for the origin of data inputs operated on by any process or system.
KERI resources:
- KERI website - https://keri.one
- KERI whitepaper - https://arxiv.org/abs/1907.02143
Deliverables of the Inputs Group
- Technical specifications for all core components required within the Inputs domain as defined by the Mission and Scope statement.
- Also check out the ToIP Deliverables document for high-level deliverables of the Trust over IP Foundation.
Semantics Group
Semantic domain [passive] / the meaning and use of what is put in, taken in, or operated on by any process or system.
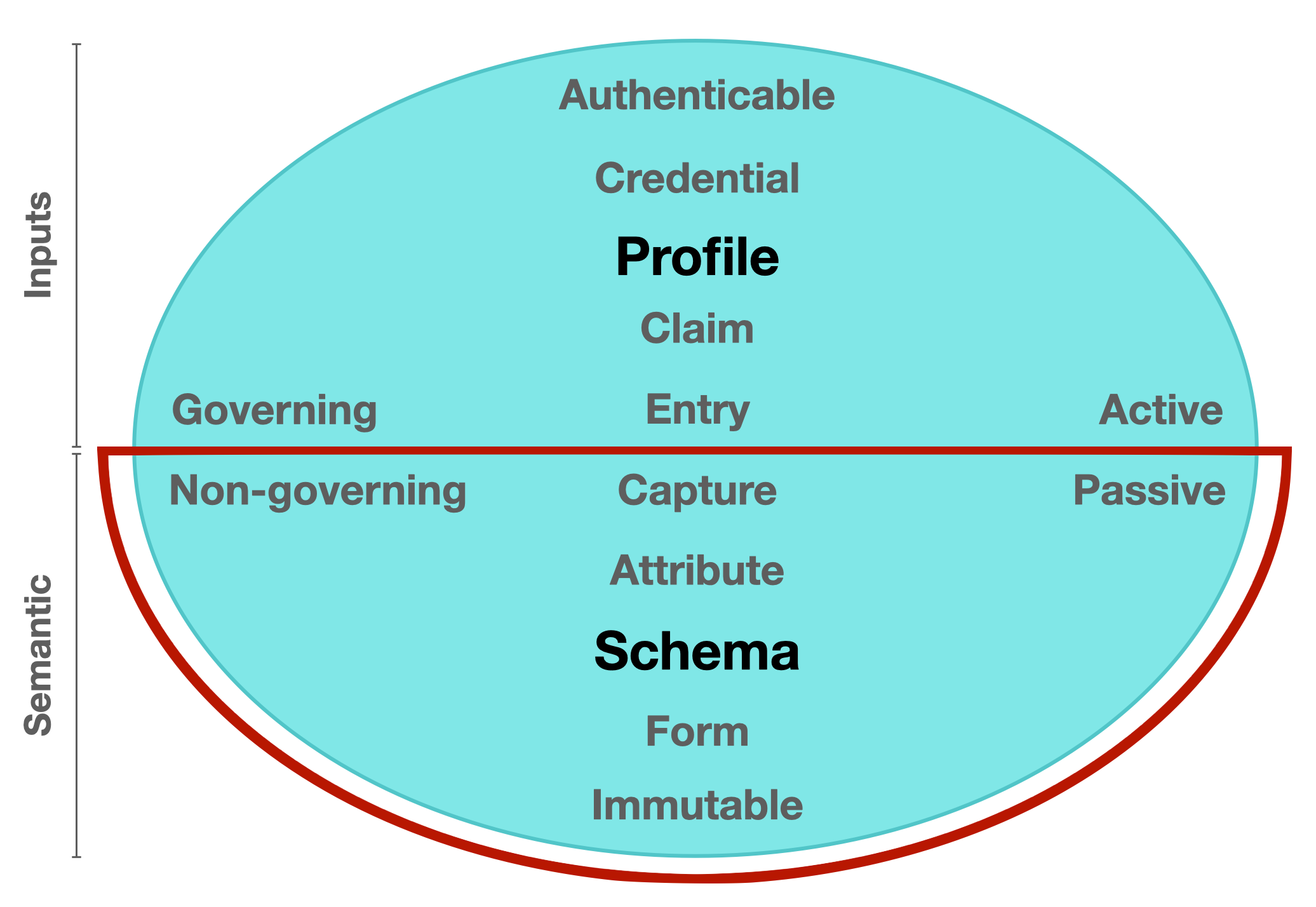
Figure 3. A component diagram highlighting the Semantic domain within a balanced network model.
Data capture is defined as the process of collecting data electronically, allowing it to be stored, searched, or organized more efficiently. In a decentralized network, data capture requires the provision of immutable fields in order to capture and store collected data. In the above component diagram, all elements and characteristics of data capture are depicted in the southern hemispherical Semantic domain.
Mission and Scope of the Semantics Group
The mission of the Semantics group (ISWG-S) is to define a data capture architecture consisting of immutable schema bases and interoperable overlays for Internet-scale deployment. The scope of this sub-group is to define specifications and best practices that bring cohesion to data capture processes and other Semantic standards throughout the ToIP stack, whether these standards are hosted at the Linux Foundation or external to it. Other sub-group activities will include creating template Requests for Proposal (RFPs) and additional guidance to utility and service providers regarding implementations in this domain. The sub-group may also organise Task Forces and Focus Groups to escalate the development of certain components if deemed appropriate by the majority of the sub-group members and in line with the overall mission of the ToIP Foundation.
Chairs / Leads of the Semantics Group
- Chair: Paul Knowles
- Vice-Chair: John Wunderlich
Core Semantic Concepts
The post millennial generation has witnessed an explosion of captured data points which has sparked profound possibilities in both Artificial Intelligence (AI) and Internet of Things (IoT) solutions. This has spawned the collective realization that society’s current technological infrastructure is simply not equipped to fully support de-identification or to entice corporations to break down internal data silos, streamline data harmonization processes and ultimately resolve worldwide data duplication and storage resource issues.
Developing and deploying the right data capture architecture will improve the quality of externally pooled data for future AI and IoT solutions.
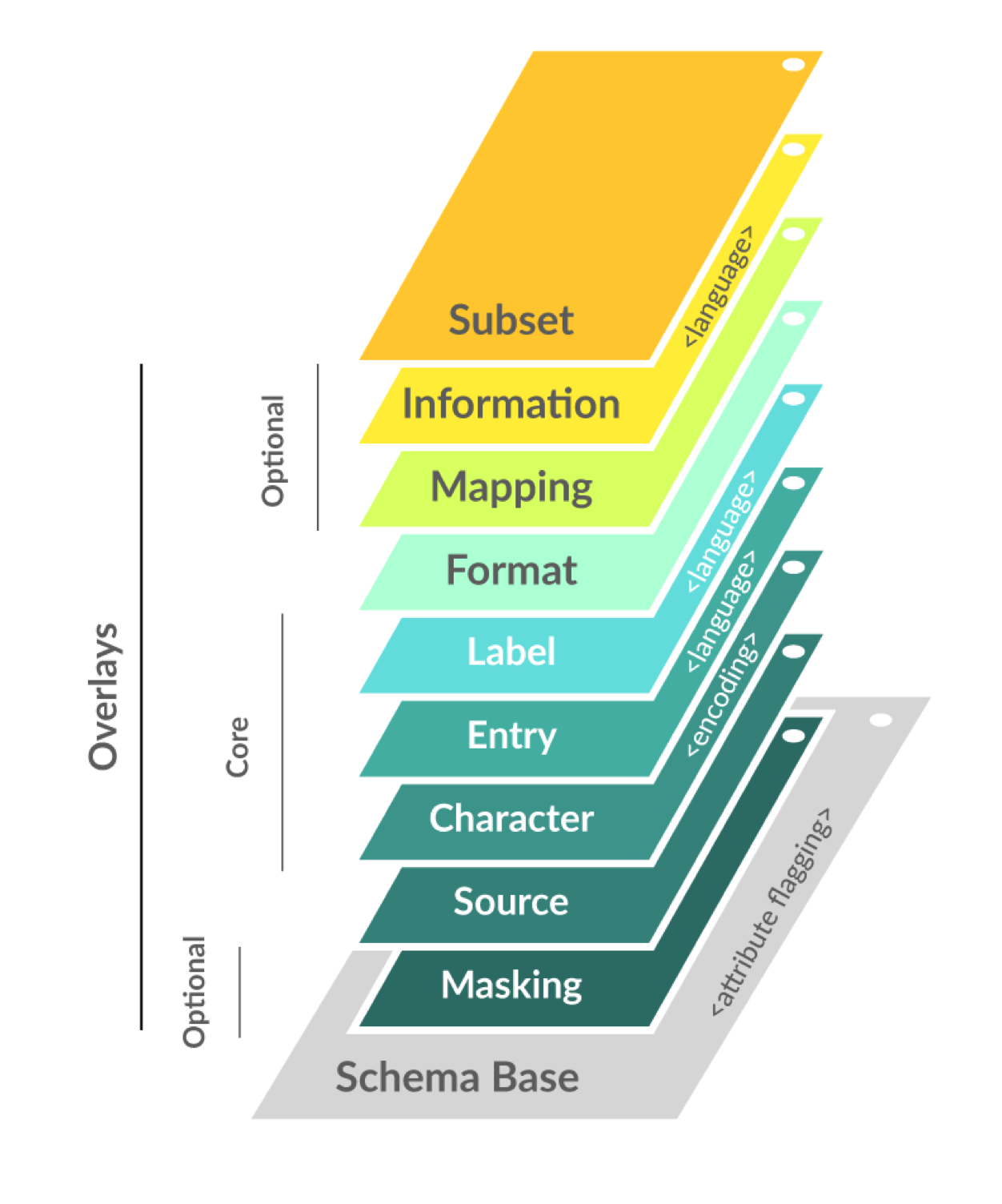
Overlays Capture Architecture (OCA)
(Presentation and live demo / Tools tutorial / .CSV parsing tutorial)
OCA is an architecture that presents a schema as a multi-dimensional object consisting of a stable schema base and interoperable overlays. Overlays are task-oriented linked data objects that provide additional extensions, coloration, and functionality to the schema base. This degree of object separation enables issuers to make custom edits to the overlays rather than to the schema base itself. In other words, multiple parties can interact with and contribute to the schema structure without having to change the schema base definition. With schema base definitions remaining stable and in their purest form, a common immutable base object is maintained throughout the capture process which enables data standardization.
OCA harmonizes data semantics. It is a global solution to semantic harmonization between data models and data representation formats. As a standardized global solution for data capture, OCA facilitates data language unification, promising to significantly enhance the ability to pool data more effectively for improved data science, statistics, analytics and other meaningful services.
OCA resources:
- OCA source code - https://github.com/thclab
- OCA website - https://oca.colossi.network
- OCA Editor - https://editor.oca.argo.colossi.network
- OCA Repository - https://repository.oca.argo.colossi.network
Deliverables of the Semantics Group
- Technical specifications for all core components required within the Semantic domain as defined by the Mission and Scope.
- Also check out the ToIP Deliverables document for high-level deliverables of the Trust over IP Foundation.