...
In privacy regulations globally transparency is a key requirement. transparency is most often represented by the requirements for notice and notification requirements in legislation are the most consistent across jurisdictions. In all regulations the identity of the PII Controller is required to be provided to the person before, at the time, or as soon as possible, when processing personal information.
This specification uses ISO/IEC standard semantics to generate a controller notice receipt for each digital identifier based relationship, and in doing so implement privacy rights to control the use of the personal information related to the identifier(s).
Problem Statement
- Security
This specification also addresses security as a part of privacy (there won't be any "considerations" at the end). Current security approaches tend to look at privacy risk less wholistically. This specification addresses this key, no pun, security challenge - for example effectively KYC enhanced with a new authorization flow that that reflects - KYB - know your business (with whom does the identifier have a relationship).
Examples include:
- Verifying people for service use as security focus
- Verfify a notice, its controller credential and its authority to process personal data
- Using an open standards framework (an appendix to this specification, e.g. ISO 29100, Kantara Notice and Consent Receipts, W3C Vocabulary for Notice and Notifications ( text which fills the receipt fields).
- Operational Privacy (Identity and Security) (Engineering) Design Principles
- Principal of "Transparency, Proportionality, and Control Reciprocity - Dynamic Data Controls"
- Next steps toward this (outside this specification)
- Code of Conduct and Practice (Ethical Operation)
- Must have a receipt (with operational Privacy Controller Credential) to engage in the Dynamic Data Control ecosystem, aka dynamic data economy, from a privacy rights and self-soveign data control perspective.
- Privacy Controller Credential is used to automate purpose driven online services, to enhance or even replace federated identity systems with self-sovering identity governance.
and specifying a legal justification and purpose for processing.
In this regard standards for the transparency and notice are required for transparency to scale. As a result there is a critical security issue in which people are not able to see who is in control of their personal data, what the legal justification and authority is used to processing personal - which makes it almost impassive to consent to transfer or exchange personal data across boarders.
This required contextual integrity.
Problem Statement
Solution
Specification Overview
Record and Receipt Info Structure
ANCR Record - (receipt prefix)
Additional Field for ANCR
- PII Controller Identifier [DiD]
- Credential ID
- Fiels specified here are added to the ANCR Notice Record,
- Accountable Person and role
- Controller Notice Record Identifier
- Controller Receipt Identifier
- : DiD: Verified Credential
- Controller Type[Ctype]:
- Notice Controller,
- PII notice controller,
- PII controller,
- PII surveillance controller , (info not provided by PII Principle)
- [Ctype] controller operator,
- Accountable Person Type
Security Considerations
2 Use Cases
- Security,
- evidence
- fraud, traceabilty
- permission and access control transparency.
- Security of Security
- schema struture and use of object identifiers
- NIST - Privacy and Security Control framework
- NIST Language -
- evidence
- Auditing a ToiP implementation
Glossary
Controller Credential & Consent Notice Semantics
ISO 29100 Privacy Stakeholders
Privacy Stakeholders | ISO Definition | |
|---|---|---|
| Regulator / | ||
| PII Principal | ||
| PII Controller | ||
| PII Processor | ||
| 3rd Party |
...
| Privacy Controller Credential Roles | |||
|---|---|---|---|
| Data Governance Authority Operator Role | Certification Providers on Regulator Approved Codes of Conduct - very limited PII - data controller personal information and a linked reference to a data subjects identifier - | ||
| Data Governance Registrar | ` |
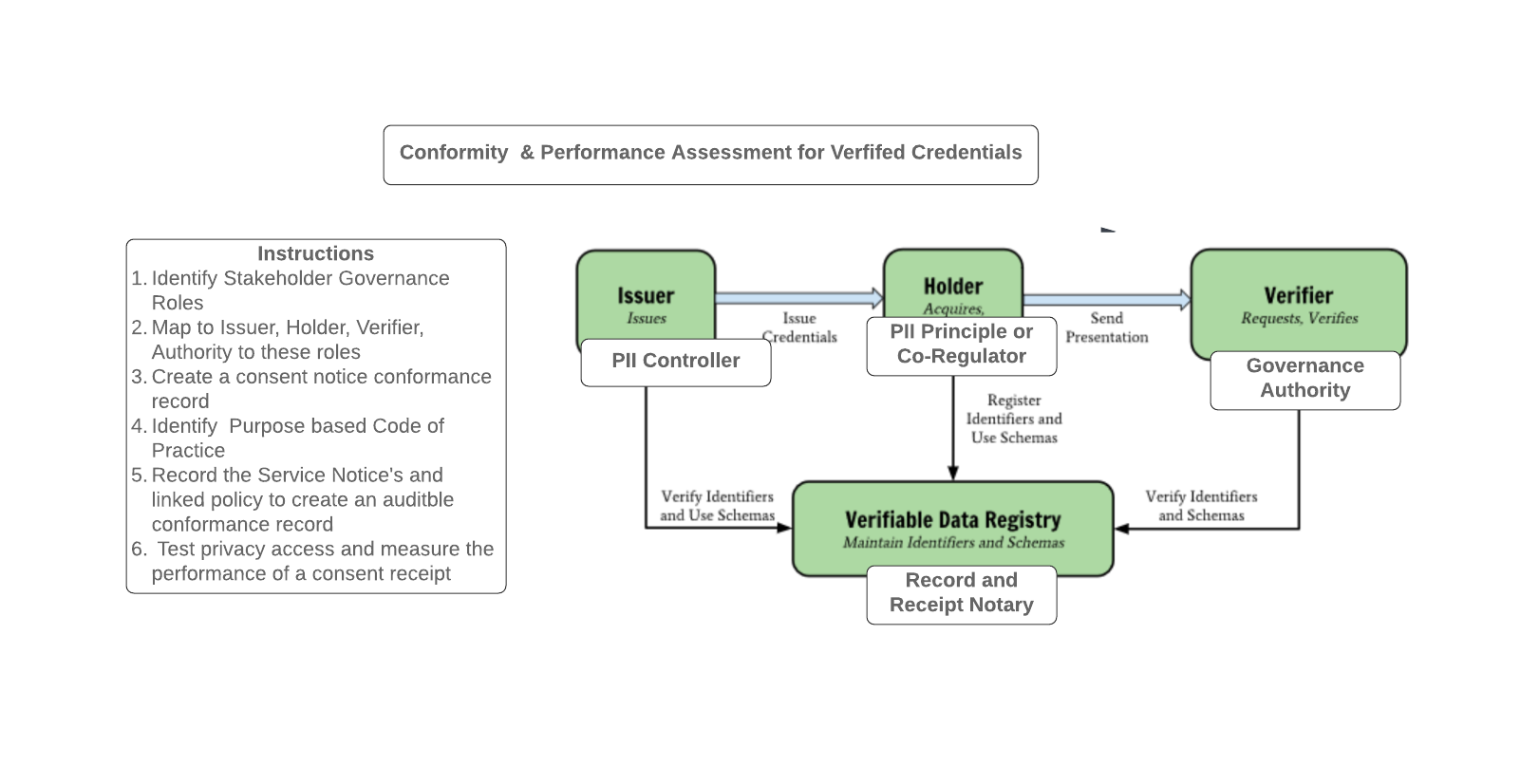
Use Case 1:
Use Case 2: Applying international governance
- Assessing a ToiP / SSI / Verified Credential Implementations
...
Legal Semantic Element | semantic description | functional usage | fields Required | |
|---|---|---|---|---|
| controller | ||||
| controller_identity | ||||
| controller address registered | ||||
| controller address (mailing) | ||||
| controller contact | extend consent termination for a control point |
...