...
Screenshots/Diagrams (numbered for reference in notes above)
#1
#2
#3
#4
#5
#6
#7
#8
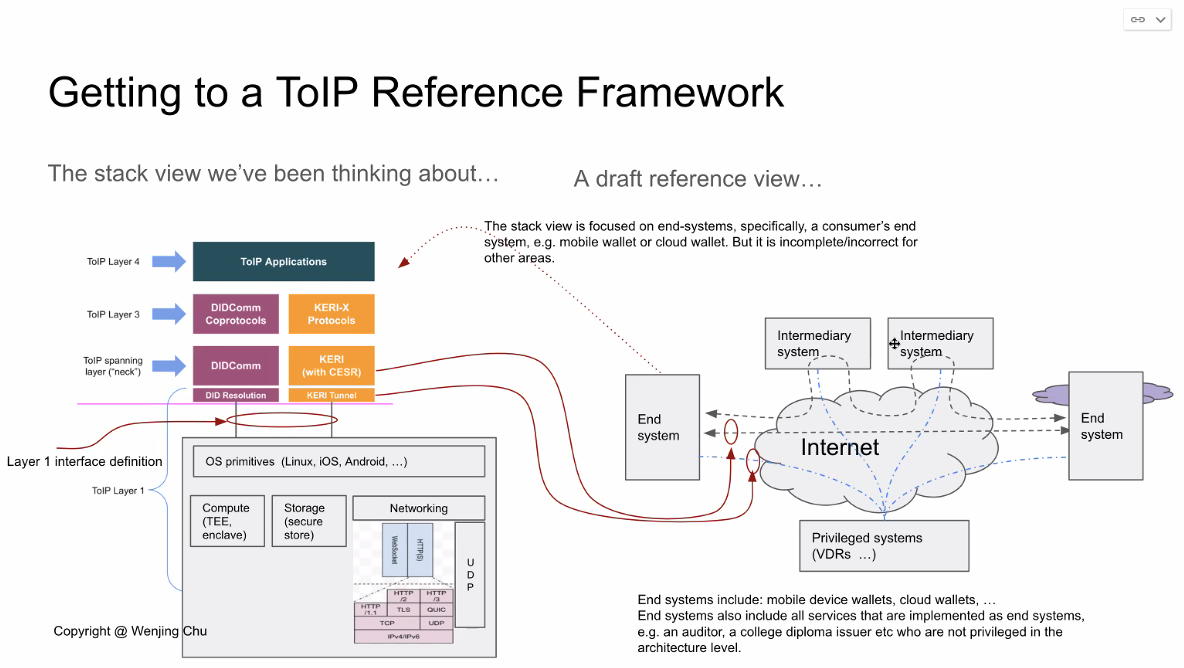
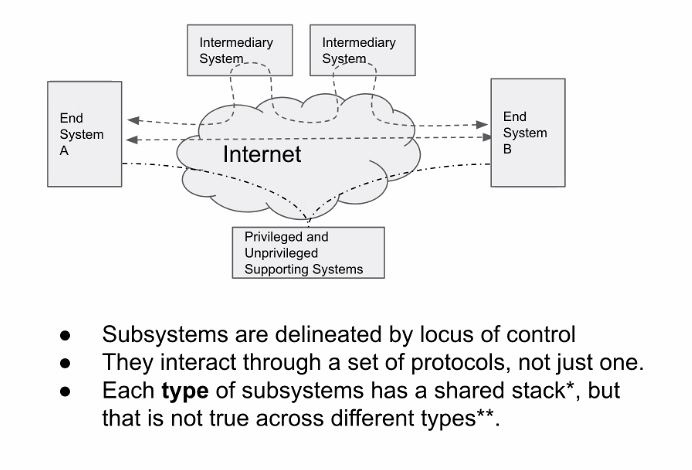
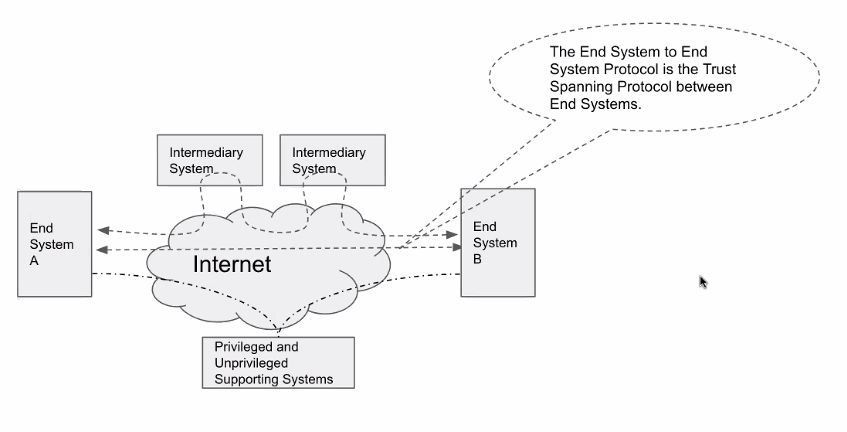
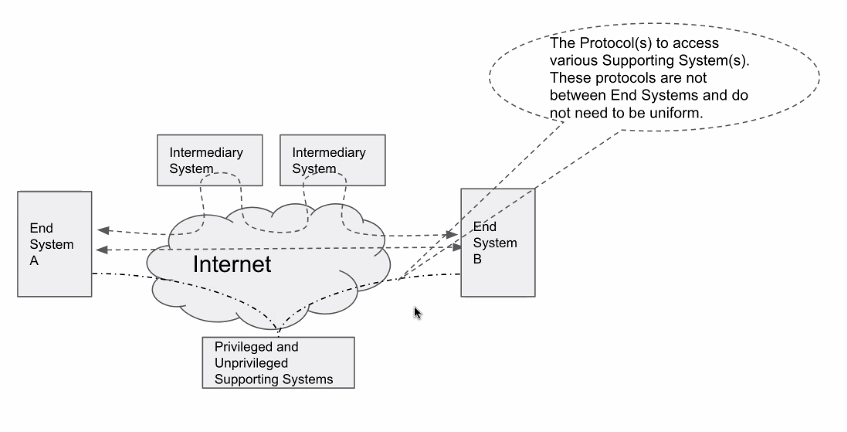
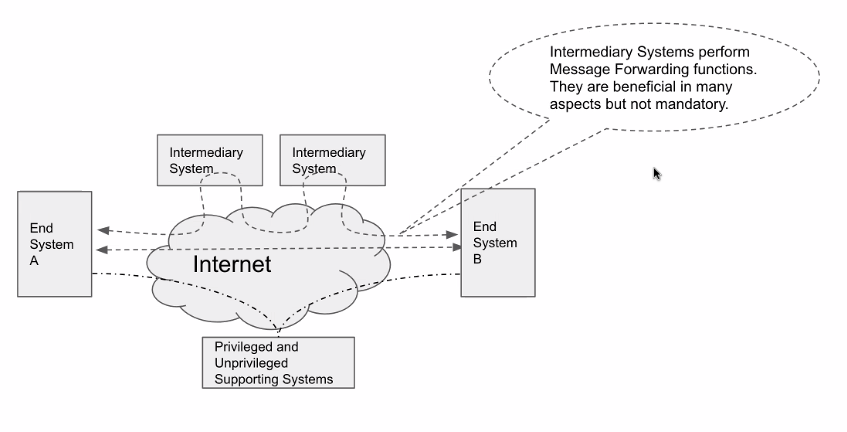
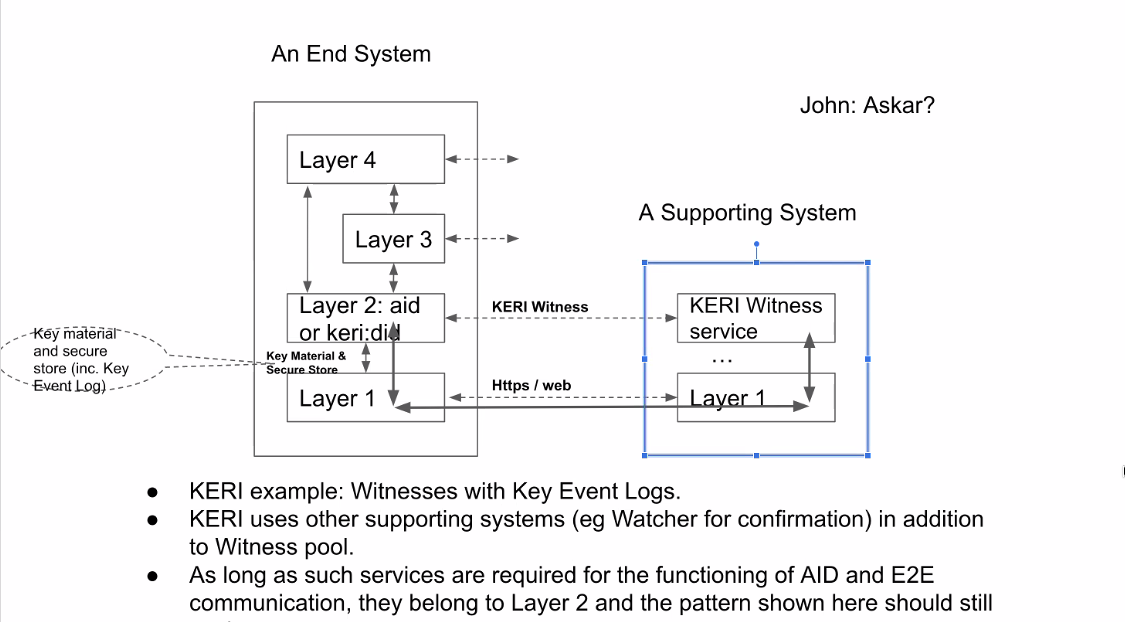
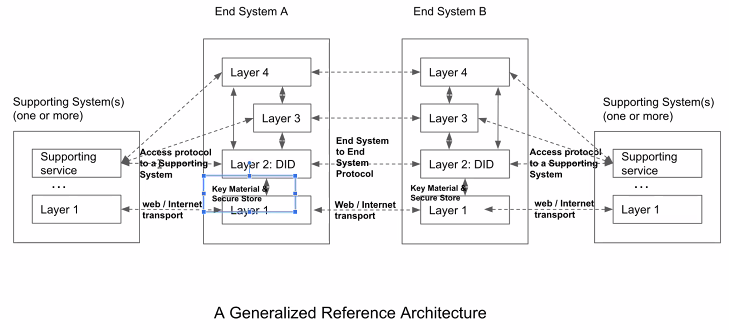
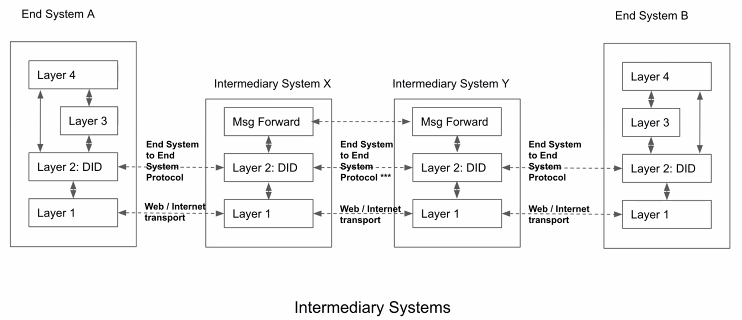
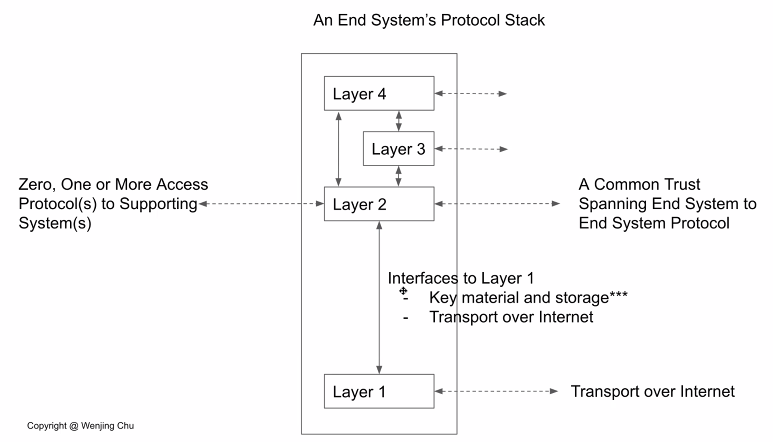
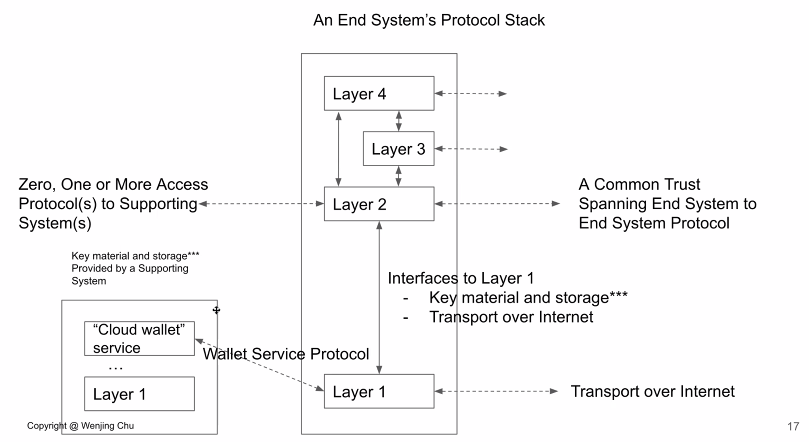
Note that the dotted arrows represent different protocols but not the actual flow of messages — that is represented by the solid arrows.
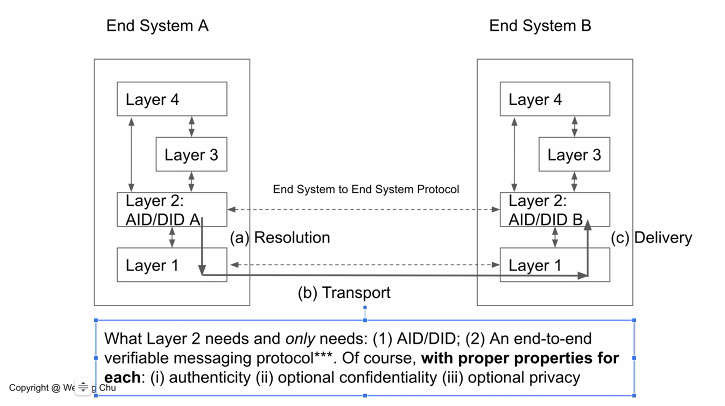
The "verifiability" in slide #8 refers to secure attribution to the source. This is the core problem we are solving in a universal way.
#9
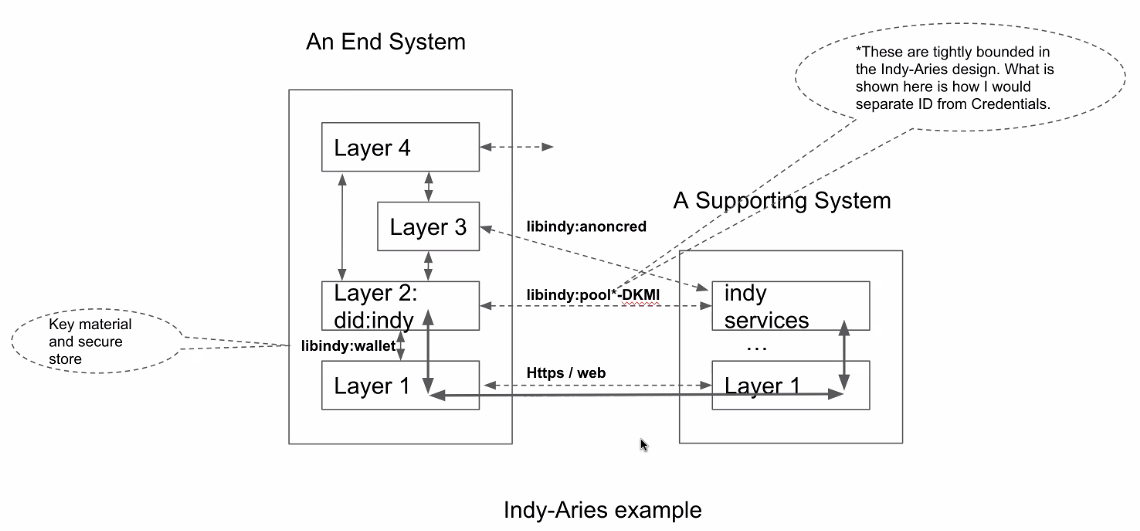
There was discussion about the separation of the "tight binding" described in this diagram. Troy Ronda shared the observation that the tight binding shown in this diagram from Wenjing Chu does not reflect how the Aries Framework Go implementation works, because it does not make the same tight binding.
Wenjing welcomed other examples.
#10
#11
#12
#13
#14
#15
Decisions
- Sample Decision Item
...