Meeting Date
The GSWG meets bi-weekly on Thursdays at 11:00-12:00 PT / 18:00-19:00 UTC. Check the ToIP Calendar for meeting dates.
Zoom Meeting Link / Recording
- Recording - skip to 6:05
Attendees
- John Phillips
- Neil Thomson
- Wendy Seltzer
- Kyle Robinson
- Callum Haslam
- Rene Solorzano
Main Goal of this Meeting
AdHoc Meeting - was out of sync with the 2-week schedule (but was still in the ToIP Calendar)
Topics Discussed:
- Use of ChatGPT for meeting notes (John Phillips provided GTP results, below)
- ToIP 3rd gen top-level diagram - Governance?
- How to present different views of ToIP for different audiences (by skills, organizational roles, different problem domains)
- Issuer Requirements as a first detailed, governance-focused requirement spec. Feedback
- SSI - Insurance and "legibility"
Agenda Items and Notes (including all relevant links)
| Time | Agenda Item | Lead | Notes |
| 5 min |
| Chairs |
|
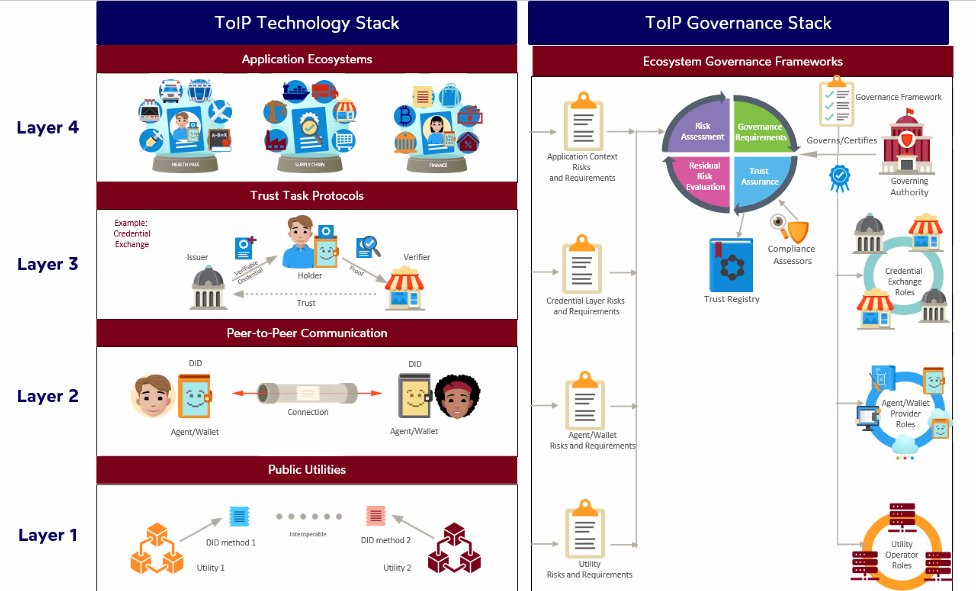
| 15 mins | All | ToIP 3rd Gen top-level diagram (governance) & different views For reference
Neil (post mtg summary): Governance is a set of risk-driven principles and approaches, which are then applied to different aspects of the technical architecture with technology, architecture, stack level specific, role and purpose-specific approaches. The current proposed Governance view as a risk-driven iterative approach is a good trade-off. However, this is still an oversimplified "marketing-ish" diagram. The discussion here on overlaying different views for different audiences. As note scribe, I've dug into the transcript, which I've paraphrased and summarized and any mistakes are mine. For more detail, watch the recording starting @ 6:05 Third Generation ToIP Diagram - how does Governance fit? Based on the GATF Slack discussions (Nov 30, 2023), this suggests a top-level view like the above, which is useful and meaningful, but without trying to be fully accurate or express all views/perspectives. And, at the next level of detail, which provides for different overlays, expanding governance from a risk assessment, requirements, assurance, auditing, etc. Like any ToIP technical service, sub-system, etc., may use components from one or more layers in the stack, other views, such as governance and operations, may have different views of the technology components that don't map 1:1 to the technical layers. This also needs to accommodate different viewers of the system (development, governance, operations, business models) There are also a wide range models: concept, logical, layering & partitioning (which is the current top-level ToIP model, implementation, workflows, data, operations (includes operations & alerting), and assurance (part of governance), trust (zero trust, auditability, verifiability) - are all candidates which need to be discussed from a risk and trust driven approach and how this is different for a ToIP approach vs. pre-zero-trust/trustworthy architectures. However, at a more detailed level, what is new and different about the ToIP approach for governance will need to be audience-focused. There are at least two types of audiences.
Explanations may need to map (for each audience) from their "understanding of how things work". Their concepts, terms and vocabulary to SSI/ToIP vocabulary, including use cases (ideally) from their domain. BCGov's "Mining Act Permit Credential" documentation (see below) reflects mapping to the Mining problem domain.
John Phillips: As with vocabulary, for diagrams for different audiences, from a ToIP perspective: "each of these needs to be consistent in the sense that from sort of an idea point of view, the way they express it and explain things, but also even from a sort of graphical point of view. They need to have some degree of commonality across the right things that are presented even down. So if you are apple, the curve on the edge of the curved boxes that we're using needs to be the same degree." John Phillips on Use Cases: to aid in explaining a broad concept, use cases have to be broadly understandable (e.g., the Bob/Alice examples in Drummond's SSI book). Use cases are, almost by definition, kind of monotheistic, a single way of looking at something, a single kind of problem. And say, if you take a travel example. someone from, say, higher education, releasing education credentials may say, "That doesn't work for me". For example, two highly detailed use cases in the Sovrin Guardianship project were very specific to a domain (and jurisdiction) that would not map for many domain/jurisdiction combinations. John Phillips: idea: generalize atomic-level actions, components and requirements that parties interact through to verify stuff, to issue things and govern things (this then lends a commonality and may simplify a set of elements used to describe ToIP to different audiences) Note: see the recording for more details 17:59 Neil (post mtg): this suggests additional models, and components similar to the issuer/holder/verifier model, say for governance and trust chains (some of the work for the Attraction Pass TF may work here. Kyle: agree with having a flashy, almost marketing picture, then applying different lenses for different audiences Neil: The Mining credentials project that BCGov is releasing may be a good example of what may be understandable in any government-regulated resource industry (logging, pulp and paper, oil and gas) John: And it's got a real business scenario. Note: John also talks about supply chain examples related to ESG (Environmental, Social & Governance) in the video Kyle: Mining Act Credential - first public credential issued. Working toward a "sustaining mining credential" (also ESG related) Neil: one of the keys to the BCGov Mining credentials is tying-back to legislation and jurisdiction which is also core to travel credentials, including data privacy concerns. Core to work in the DIF Hospitality & Travel SIG is a comprehensive travel (traveller) profile, which is PII/Personal data on steroids, and as travel is frequently across multiple jurisdictions, privacy compliance will not be trivial, which may require data models which can be annotated with what data/properties are sensitive. John: provides an example that on consent for what PII/Person data shares (birth date), cross-jurisdictional cases may not be possible for code to solve, it likely has to be left up to the user to decide, the issue is ow to ensure the user is making an informed decision/discretion. Issuer Requirements - first draft complete - feedback and next steps? John: feeling the document is too complicated. It's one thing to provide that level of detail to experienced ToIP members, such as BCGov, but it may be more of a detailed companion guide, and perhaps there is a simpler to requirements specification. Discussion, Perhaps the current version is overly prescriptive. Using the example of key rotation, perhaps provide minimum requirements, plus desirable requirements, with a worked example of both (e.g., KERI as the desirable requirements example) ? Perhaps all an Issuer has to do is to to explain is what kind of key rotation management they use, it's algorithms, etc. It's up to them to work the details. ToIP doesn't need to tell you how to manage your keys. Kyle: Is the Issuer Requirements document a template to be filled in, or guidance? Neil: It's predominantly guidance and specifies a few MUSTs, but has a great deal of SHOULD (recommend) and MAY (optional). Its core approach recommends that Issuer requirements be risk-driven, which is required for all aspects of any ecosystem and its components. Kyle: Is the target for the ecosystem level (all your issuers must meet these requirements or is the target an individual issuer? Neil: That's up to the ecosystem as to whether all its issuers must meet the same level of requirements John: This does raise the question, should this be a ToIP Specification (which defines ToIP compliance)? And if so is there a certification program/body and services (Neil - which the OIDC foundation does), including compliance test suites)? Or perhaps it falls on the ecosystem and components it to define why they are trustworthy and provide ways in which you might check that, including how they are governed. Asserting all components, governance, etc. be ToIP compliant may be a barrier to entry, vs. an existing system which incrementally upgrades their compliance, including being transparent on how they are trustworthy. Can see both levels of compliance Kyle: two aspects of trust - do you trust the ecosystem and governance, and do you trust the technology, which includes things like key rotation mechanisms? The Issuer Requirements, I think speaks to both sides, but mostly technical. And then there are cybersecurity aspects that are not specified (so far, by ToIP). Insurance and "Legibility" Neil (post mtg) : Legibility - a working understanding of "legibility" for tech built on something like ToIP, is how easy is it to understand ToIP and ToIP-based implementation? Adoption requires bridging the gap from non-ToIP. Wendy - other aspects - (cyber security) insurance and legibility. Insurance from the perspective of, "if something goes wrong, how am I "made whole"". Interoperating ecosystems, which may use different approaches, but there needs to be some legible interface (e.g., APIs) to the ecosystem components and operations/governance in order to interoperate and to trust. John: Encountered insurance questions in 2017 - if I'm provided this claim as a verifier, can I get someone to insure me against it being false? And what would I have to pay for that insurance? Neil: Scott Perry brought in HITRUST (recorded (2023-7-27)), which provides "information protection standards" and is a certifying body for organizations to demonstrate their governance and technology with cybersecurity, data protection and risk mitigation. I asked how organizations justify the expense and organizational time commitment. The answer was a reduction of cybersecurity insurance by as much as 50% Trade-off - using ChatGPT-4 for meeting minutes (summary) vs. human notes Based on in-meeting human notes and digging through the recording, GPT misses some key points and details, which, in hindsight:
|
Chat GPT Summary/Minutes
John Phillips - two versions of GPT-4 use, I prefer the first since it makes us more human
Governance Stack Working Group Meeting 2023-11-30
ChatGPT minutes
Created from a ChatGPT 4 session prompted with the attendees, meeting objective, transcript and chat discussion…
ChatGPT Coached/Prompted by John Phillips (so you know who to blame…)
Some formatting recovery for bulleted lists etc. Any material additions have been put in square bracket parenthesis (“[“,”]”)
Two versions, the first where I had to separately prompt for the chat messages to be interpreted, and the second where I asked for a consolidated version.
Keen observers will notice a change of tone in the two versions, the first seems more congratulatory/celebratory, the second more prosaic. My prompts didn’t ask for this change. Basically we need to be cautious about any AI-generated content as it will have colour, emphasis and even content that we may not have asked for…
[Version 1] Summary of Trust over IP Governance Stack Working Group Meeting:
[Version 2] Consolidated Summary of Trust over IP Governance Stack Working Group Meeting
[Version 1] Summary of Trust over IP Governance Stack Working Group Meeting:
Attendees:
- Wendy Seltzer
- John Phillips
- Neil Thomson
- Kyle Robinson
- Rene Solorzano
- Calum Haslam
Objective:
To discuss current activities and work in progress across the group.
Key Points:
- John Phillips and Neil Thomson initiated a light conversation about personal experiences related to early morning activities and trail running, reflecting on risk assessments in different contexts (e.g., cycling, running).
- Neil Thomson raised a concern about the lack of updates in Slack regarding specific discussions, hinting at the need for better communication or tracking.
- John Phillips discussed the use of AI to synthesize meeting transcripts. He noted the technology's effectiveness in clarifying discussions but also its limitations in accurately capturing dialects and accents.
- Neil Thomson added insights about the AI's limitations, particularly with minority accents, emphasizing the need for diverse data training.
- Discussion shifted to working group topics, led by John Phillips and Neil Thomson. They delved into the Architecture Task Force, discussing the challenge of choosing a cover image to represent the Trust over IP model and the importance of varying perspectives in diagrams.
- Wendy Seltzer updated on her progress with the membership agreement and accessing group documents.
- Neil Thomson and John Phillips explored the concept of governance layers within the Trust over IP framework, discussing how governance provides an overarching structure to the technology and protocols in place.
- Kyle Robinson chimed in briefly, agreeing with John's point on having a representative image for the Trust over IP and the need for different lenses at various working group levels.
- John Phillips and Neil Thomson discussed the importance of use cases in explaining the Trust over IP model, with John cautioning against being overly specific to ensure broad applicability.
- Kyle Robinson brought up the implementation of digital credentials in mining, highlighting the real-world application of the Trust over IP principles.
- The conversation then focused on the importance of clear governance and technical standards for issuers within the Trust over IP framework, discussing how these standards could influence trust and insurance costs.
- Wendy Seltzer brought up the concepts of insurance and legibility within the framework, emphasizing the importance of understanding interfaces and having recourse in case of failures.
- The meeting concluded with a discussion on how the Trust over IP framework could be applied and adapted across different industries and use cases, with a focus on maintaining consistent standards and governance models.
The meeting was productive, with valuable insights and discussions on various aspects of the Trust over IP framework, particularly focusing on governance, use case diversity, technical standards, and real-world applications.
Chat Messages:
- Kyle Robinson shared links to the production versions of governance documentation related to Mines, specifically the Major Mines Office and Mines Act Permit. This provided attendees with direct access to current governance documents in practice:
- Major Mines Office: https://bcgov.github.io/bc-vcpedia/applications/major-mines-office/governance.html
- Mines Act Permit: https://bcgov.github.io/bc-vcpedia/credentials/bc-mines-act-permit/1.1.1/governance.html
- He also provided the link to the GitHub repository for further details: https://github.com/bcgov/bc-vcpedia.
- Rene Solorzano expressed gratitude for sharing this information, and Kyle Robinson acknowledged this with a thumbs-up emoji.
- Towards the end of the meeting, Kyle Robinson announced his departure, thanking everyone and wishing them a good day.
- John Phillips referenced Wendy Seltzer's earlier points, suggesting she look into the work of Paul Knowles in the Trust over IP groups, particularly the Overlay Capture Architecture, for ideas on portability and interpretability.
- Wendy Seltzer thanked John for the suggestion.
- Neil Thomson shared his email (neil.thomson@queryvision.com), presumably for further discussion or follow-up.
These chat messages added context to the meeting, offering resources and contacts for deeper understanding and collaboration on the Trust over IP framework and its applications in different sectors.
[Version 2] Consolidated Summary of Trust over IP Governance Stack Working Group Meeting
Attendees:
- Wendy Seltzer
- John Phillips
- Neil Thomson
- Kyle Robinson
- Rene Solorzano
- Calum Haslam
Meeting Objective:
Discussion of current activities and work in progress across the Trust over IP Governance Stack Working Group.
Key Discussion Points:
- Neil Thomson and John Phillips initiated a conversation about meeting timings and personal activities.
- John Phillips expressed concerns about the potential risks of biking early in the morning and shared his experience with AI-powered transcript synthesis.
- Neil Thomson discussed the inaccuracies of real-time transcription, especially with accents, highlighting the challenges faced by AI in understanding diverse accents.
- John Phillips and Neil Thomson delved into a discussion on the Trust over IP architecture, emphasizing the need for diverse perspectives in diagrams and the importance of choosing a 'cover image' for the Trust over IP website.
- Wendy Seltzer chimed in regarding her progress with signing the membership agreement and waiting for document space access.
- Neil Thomson and John Phillips continued to discuss governance and architecture layers, stressing the importance of having multiple views for better understanding.
- Neil Thomson elaborated on the governance stack's layers, addressing the issue of fitting a four-layer vertical diagram into the architecture.
- John Phillips and Neil Thomson further discussed the challenges and strategies in presenting the Trust over IP architecture, including the need for a consistent graphical representation across different views.
- Kyle Robinson joined the conversation, emphasizing the value of a clear and appealing front-page image for the Trust over IP website.
- Neil Thomson, John Phillips, and Kyle Robinson explored the applicability of Trust over IP principles in different industries, such as mining and travel.
- Neil Thomson talked about the importance of data privacy and jurisdictional considerations in developing trustworthy systems.
- John Phillips raised concerns about the issuer requirements document, debating its complexity and potential over-prescriptiveness.
- Kyle Robinson and Neil Thomson discussed the challenges and considerations in governing multiple issuers and the significance of trustworthiness in both business processes and technical practices.
- Wendy Seltzer introduced the concepts of insurance and legibility in trust systems, prompting a discussion on the role of insurance in establishing trust.
Chat Messages:
- Kyle Robinson shared links to governance documentation related to Mines:
- Rene Solorzano thanked Kyle for sharing, which Kyle acknowledged.
- Kyle Robinson had to leave the meeting early.
- John Phillips recommended Wendy Seltzer to explore Paul Knowles' work on the Overlay Capture Architecture for insights into portability and interpretability.
- Neil Thomson shared his email for further communication.
These minutes and chat messages reflect the comprehensive discussions and shared resources in the Trust over IP Governance Stack Working Group meeting, highlighting the collaborative efforts and diverse perspectives within the group.