...
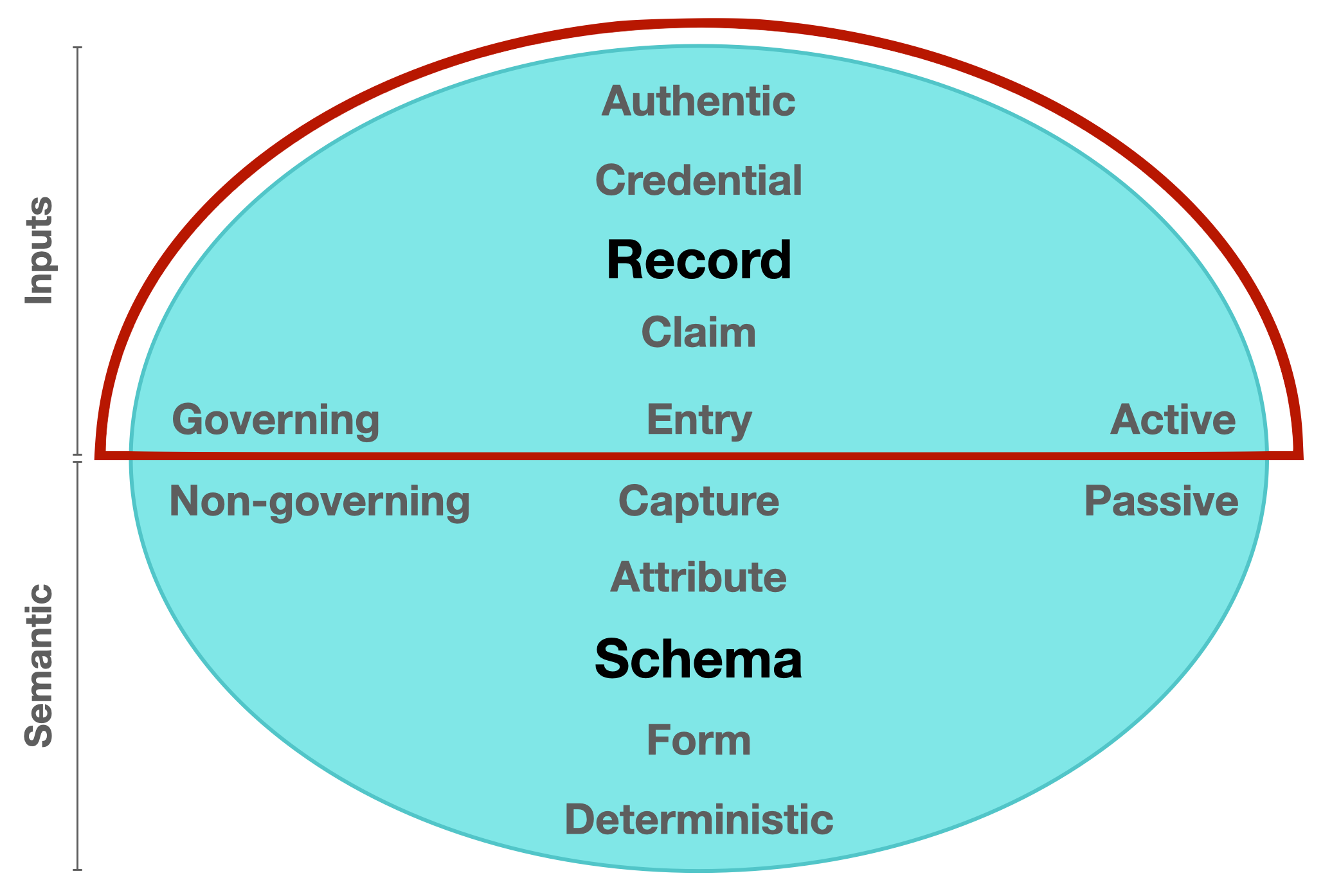
Inputs domain [active] / what is put in, taken in, or operated on by any process or system
Figure 1. Model of Identifier States (Active state). A component diagram highlighting the Inputs domain within a balanced network model.
...
KERI is an architecture that offers information uniqueness from captured entropy by compiling the history of all uses or changes to the public/private key pair. This is achieved by universal self-certifying proofs of the binding between the self-certifying identifier (SCID) and the associated public/private key pairs. It is a truly decentralized key management solution offering the strongest possible levels of pseudonymity, ledger-less identifiers and separable identifier assurance bases for all network participants.
KERI is a secure overlay for the Internet where any digital representation of a governing entity can serve as an autonomous self-certifying root-of-assurance. It is a solution that offers secure data control established via self-certifying pseudonymous identifiers. As a standardized global solution for data entry, KERI facilitates sapored data supply chains, enabling a record trail that accounts for the origin of data inputs operated on by any process or system.
...