2022-04-25 BGBU TF USA/EU TF Meeting
15.00 UTC = 8:00 PT = 11.00 ET = 17:00 CET = 20:30 IST Zoom Meeting Link https://zoom.us/j/97159895478?pwd=emFjbU8xdWs0dE5iaE0zeDVZREFYQT09
MEETING RECORDING
Attendees: Nicky HickmanDarrell O'Donnell, Phil Wolff, Jacques Bikoundou, Christine Martin
Agenda
2022-03-17 SSI Harms APAC TF Meeting
6.00 UTC = 22:00 PT = 7:00 CET = 10:30 IST = 17:00 Melbourne = 13:00 Thailand Zoom Meeting Link https://zoom.us/j/95121109567?pwd=UFBrWU5PcC9RZS9UaFg1UG81WGZZdz09 Meeting ID: 951 2110 9567 Passcode: 082179
MEETING RECORDINGRECORDING
Notes from the APAC Meeting are recorded in the Table below in green text
Attendees: Nicky Hickman sankarshan Jo Spencer John Phillips
...
| Time | Item | Lead | Notes |
| 5 min | | Darrell | |
| 5 mins | Intro's new members & Updates | All | Updates - Discussion re moving meeting to 11am PT = 14.00 ET = 18.00 UTC = 19.00 BST = 20.00 CEST - put in slack question to group to move.
- Links & References: Please use this Responsible Tech Resources page to capture links to media or online resources that can help us with our work. Responsible Tech Resources All are updated now
- SSI Harms now changed on wikis, slack & calendar invites etc to BGBU
- Our First Deliverable Storyboard, is open for business here. Aim is to have key questions/ discussion points ready for IIW by end of month - no group members attending so use another mechanism to challenge our thinking later on in our process.
- Sankarshan working on voting and democracy work, Nicky attended APPG on blockchain & voting, and some interesting perspectives from Robert Herian on the dangers of blockchain & voting voting https://www.researchgate.net/publication/339353856_Blockchain_GDPR_and_fantasies_of_data_sovereignty
- Danger of using global south as a set of experiments - urgency and pragmatic approaches vs north america, problem not a strong representation from Latam. Similar to clinical trials - now happening with financial services and digital products, identity, identifiers etc These are specific harms. EG health privatisation e.g. HealthID. We can't look at SSI on its own, must be in connection with the businesses and services it enables. Decentralization also leads to other things if left unchecked. All 'sold' as discovery - but in effect it's service providers discovering you.
- Consider 3 pillars of inclusion = connection, identity, value exchange
- Must at least ensure that folks are not worse off as a result of these developments. Problem of data silo's even within decentralized systems. Always going to have one player that gets more and more data and has undue influence within the market. Data breeds data.
- Virtual IIW - let's make a proposal to Phil, Doc & Kaliya
- Indigenous group, example - document the concerns, position paper (problem definition), capture the needs at the margins. Good example of common problems but highlighted because they are at the edge/periphery. Document real-world problems and impacts.
- problems of colonial past, current harms of centralized state systems.
- Structural biases that are embedded in our own frames of reference, e.g. UN. eg identity & violence book. Also aboriginal man who Stan Grant. https://www.booktopia.com.au/on-identity-stan-grant/book/9780733644238.html
Even naming is deeply politicised, internet meme 40 different ways that coders get names wrong. - HARM! not being able to use your own name - = identifier, can have many names - in West is a unique and fixed identifier.
- Anglo-Indian names have ' in them - Aadhar can't accommodate names with apostrophe - but PAN does, so Aaadhar overwrites the name in PAN then creates authentication problems. 'why should I have to change my name if the states' ID system is poorly coded'
- How can vulnerable people be cared for online?
- CO-CREATION - Group needs representation from those we seek to support / help / protecting. We understood representation from 'real people'
- Need to be engaged now - up front to own the process. We are promoting a model of digital interaction which we think is a good thing, but we need to understand the existing digital access/ interaction and then understand from them as to how VC's - pre-mortem / pre-parade, if this were successful what would happen, if things went wrong what could cause that?
- Groups definition
- understand challenges in working digitally with specific groups in the community
- use exclusion factors?
- power imbalances & poverty of human dignity at heart of all harms
- Start with recognition
- Goldilocks not too much identification, not too little, just enough for the purpose (Kim's 2nd Law) - Harm with issuance, and then when you have to use it.
- Evolving framework / discussion as with guardianship
|
| 5 mins | Update on Actions from Previous Meetings | All | - ACTION - Darrell to clone storyline format (from Drummond)
- ACTION - ALL to review background links (on Purpose page under Links & Files)
- ACTION - Persona Development (lapsed)
- ACTION - reach out to others to join or be an 'expert witness' - open for follow up after we have more clarity on scope and basic storyboard.
- John Phillips to ask https://sigchi.org/ if they have any kind of framework for assessing interaction harms
- Nicky Hickman to get kinship structures / forms from anthropology notes https://docs.google.com/document/d/1WQCD9floOebL2716PHZBZ8a-JvMdwb-rdx02hkQdfns/edit
- Eric Weltonto discuss domicile law and issues related to documentation and also on biometrics work next time. Bound carefully with exam question. Close during that session.
|
| 30 mins | Discussion Scope: Root Cause Analysis & Frameworks | Nicky | Scope & clarification from USA Call - Suggested from USA call - that we de-scope to only focus on the new harms that could arise from use of SSI - do we agree?
- e.g. Over-identification
- How do we de-scope without removing before / after. IE what's the cut-off function?
- Specifically addressing the deployers of technology in ensuring that their deployments do not unwittingly increase threat surface/vectors to users (holders) causing harms. The deliverable should describe the harms, how they arise, how they can be mitigated and recourse for victims, e.g. responses could include pooling risk or sharing harms, detect, intervene & recover. - Incidence response approach. EG in detection how can you tell if things are going wrong, so you might monitor or surveille to ensure that harms not involving malicious actors for example are alerted and acted upon.
- Support from USA group to use persona for storytelling, but interview real people on the ground to carry out research and understand harms.
- Recommendation from USA group that we do not exclusively focus on marginalized or vulnerable people, as we are all vulnerable at different times of our lives (e.g. as children, as frail elderly), however using extreme users or edge cases as persona can support robust design
Root Cause Analysis? - Is part of the problem that many think SSI is specifically designed to address harms of Web 1.0 & 2.0?
- Is part of the problem that SSI is designed with a specific Western Educated Industrialised R Democratic perspective on the nature of human identity, the format of families, marriage, kinship and naming conventions? An ego-centric (individual) rather than socio-centric (dividual) view of identity.?
- Must go deep to challenge the underpinnings of SSI - the problem of digital imperialism
- One core under-pinning value is personal agency - this is based on principles of 'free will', this in turn is tied up with our ideas of free speech, free trade and is baked into our belief systems. This is why it is so challenging.
Possible Frameworks: - Creates or uses existing framework for analysing the dangers, risks, potential harms and threats (DRiPHT) to people with a particular focus on excluded, marginalized or vulnerable people.
- RIGHTS-BASED sankarshan's Digital Identifiers & Rights
- HARMS -BASED Me2B Alliance Digital Harms Dictionary. Uses DJ Solove's Privacy Taxonomy or Koops et al Typology to classify digital harms
- Action: Nicky to ask Lisa if we can have Digital Harms Dictionary in usable form to evaluate.
- ROLES - BASED: What are the unintended consequences of SSI or digital ID benefits on our chosen persona: Children, Refugee, Indigenous People: e.g. McKinsey. Digital Identification, a key to inclusive growth or Kaliya Young The Domains of Identity
  4. SECTOR-BASED - prioritizing the primary sectors of uptake that ToIP members want us to look at and which impact against sustainable livelihood outcomes Healthcare Public Sector National Identity & Legal Identification Financial Services & Fintech 5. OUTCOMES-BASED Sustainable Livelihoods framework . Based on the principle that your digital data is a livelihood asset, a new form of capital? Or a digital representation of other types of capital? Harms arise when the outcomes or consequences negatively impact positive livelihood outcomes - More income
- Increased wellbeing
- Reduced vulnerability
- Improved Food Security
- More sustainable use of NR Base
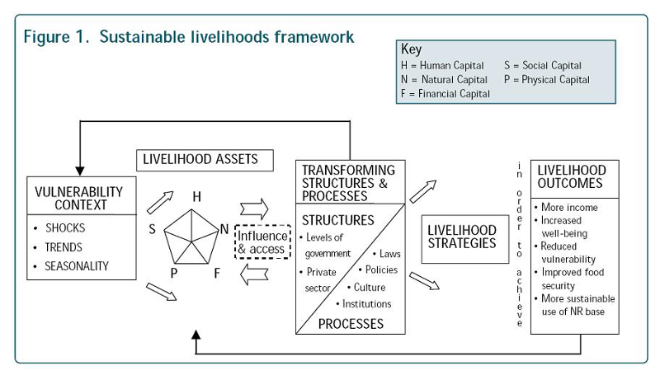
More likely a combination of a couple of these? Discussion - starting more messy and coming to frameworks, e.g. start with one harm and build out an approach of key questions: - How does it arise?
- Who does it impact?
- How can it be detected
- How can it be mitigated? (intervention)
- How can it be set right? (recovery)
Can also have ideation session - dropping a long list of harms - reference powerpoint storyboard - put in slack for other sto update then add one harm with above questions to get started. |
| 10 mins | Storyboard | Darrell | |
| 5 mins | Close & AOB | Nicky | - Get Me2B Alliance to allow access to harms dictionary for evaluation (Nicky)
- Put in Slack alternate meeting time proposal (Nicky)
- Encourage all to add to storyboard (Nicky)
|
...


