...
Data entry requires a signing key in order to establish that inputted data has come from an authenticable authentic source. Authenticable Data entry items are identified by active identifiers.
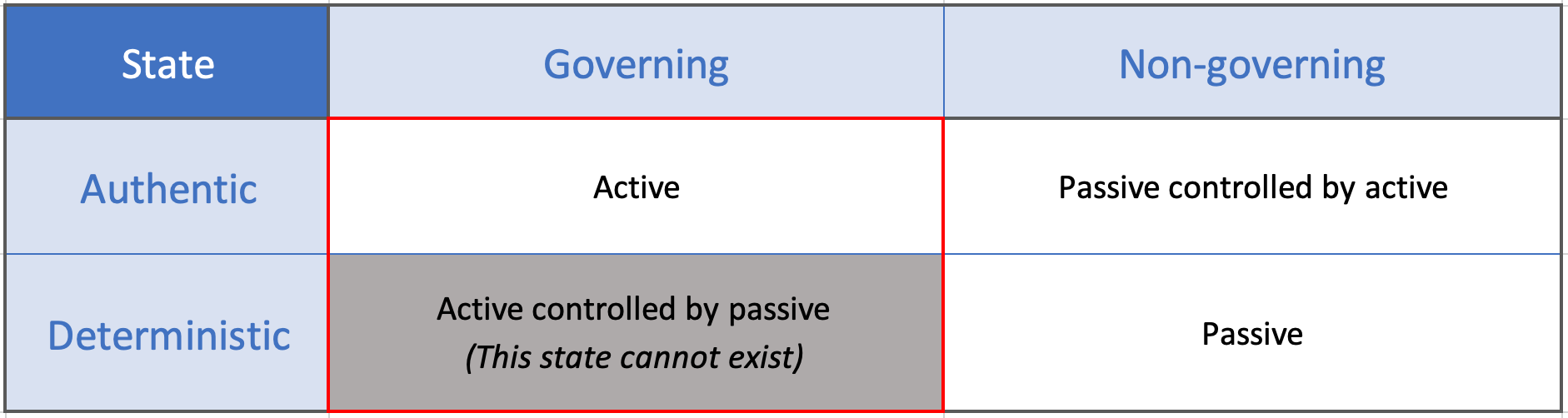
Table: A hash grid table describing the different states of active and passive identifiers. The states of active identifiers are highlighted.
What is an Active identifier?
An authenticable identifier used identifier that originates from an authentic source to identify an entity which that has the capacity to govern. An active identifier cannot be controlled by a passive identifier.
...