NA/EU
APAC
1) Discuss the recent FIDO white paper. and any implications for the ToIP stack, 2) continue discussion of feedback on the storyline deck of layer-by-layer requirements.
| Time | Agenda Item | Lead | Notes |
| 5 min |
| Chairs |
|
| 5 min | Announcements | All | Updates of general interest to TATF members.
|
| 5 min | Review of previous action items | Chairs |
|
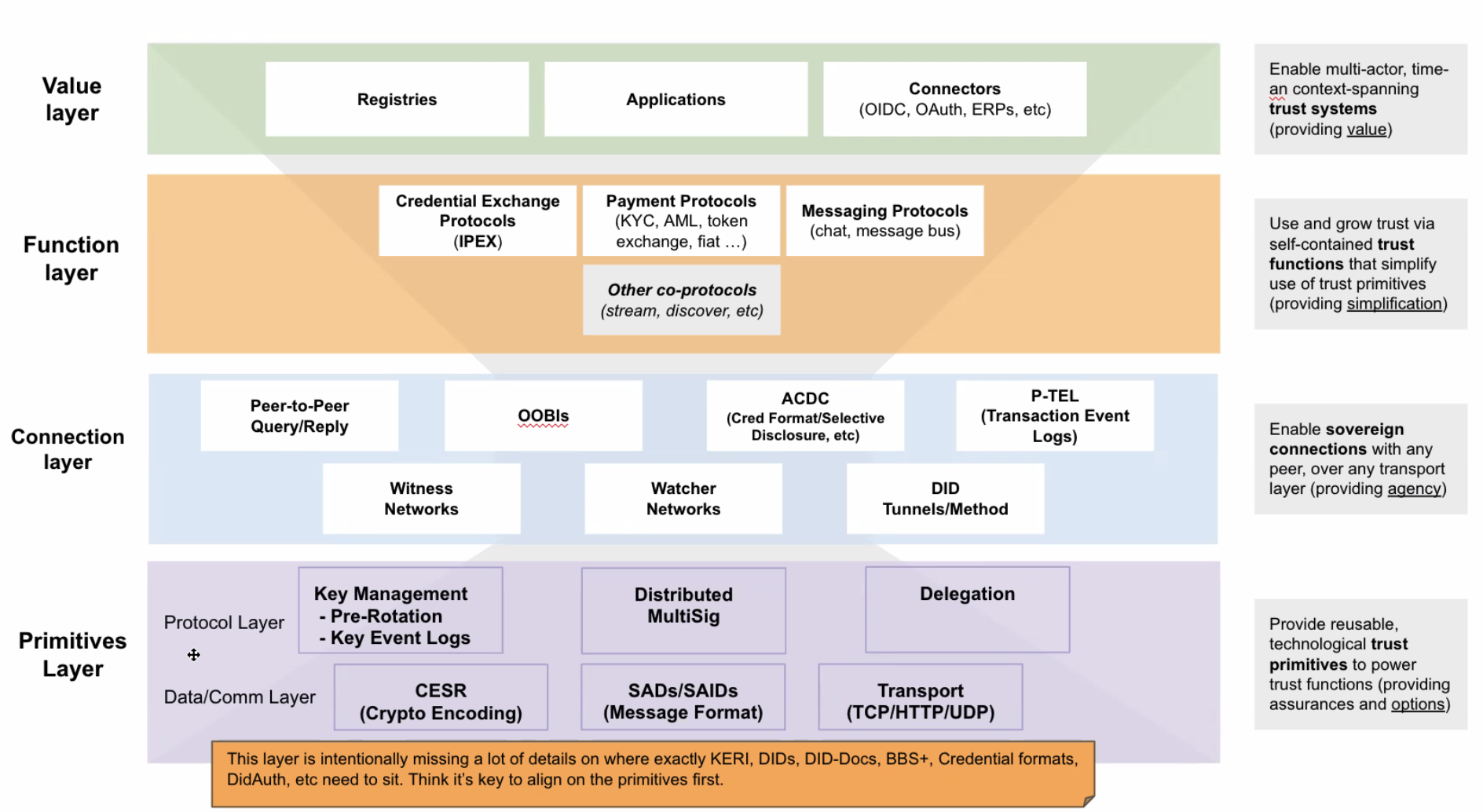
| 15 mins | The KERI / ACDC "stack" | Phil Feairheller | Per the first action item above, Phil shared a diagram (screenshot #1 below) of how all the component pieces/specs for KERI and ACDC fit within the four-layer ToIP stack. (This diagram is now part of the ToIP Protocol Stack Diagrams Google Slides deck.)
ACTION: Drummond Reedto add chained root of trust topic to the agenda for next week's calls. ACTION: Drummond Reed to add spanning layer discussion to the agenda for next week's calls. |
| 15 mins | FIDO white paper discussion | Continue a discussion that started on the ToIP Slack about the recent FIDO white paper. Wenjing Chu posted this: There’s a lot to learn here. I’d like to highlight one - we need a proper mental road map for the development of a complex ToIP stack. AKA a life cycle model. Reactionary mode can be exciting but ultimately not most productive.
DECISION: The TATF shall develop a roadmap for the evolution of the ToIP stack, a summary of which should be included as a section in the ToIP Technology Architecture Specification V1, in order to make it clear what are the canonical use cases and scope limitations for the V1 ToIP stack. ACTION: Drummond Reed to make the first agenda item for next week's meeting a discussion of the canonical use cases and scope limitations for the V1 ToIP stack. ACTION: Drummond Reed to start a discussion on our Slack channel about the canonical use cases and scope limitations for the V1 ToIP stack in preparation for next week's meeting. | |
| 20 mins | Continue review of comments on requirements | All | Continue our review of requirements in the storyline deck of layer-by-layer requirements. Our goal is to move into drafting the Google doc version of the spec next week. (All slide numbers are of 2022-03-31).
ACTION: Drummond Reed to prepare a revised outline of the Google doc version of the ToIP Technology Architecture Specification for review at next week's meeting. |
| 5 mins |
| Chairs |
#1

ACTION: Drummond Reed to start a discussion on our Slack channel about the canonical use cases and scope limitations for the V1 ToIP stack in preparation for next week's meeting.
ACTION: Drummond Reed to make the first agenda item for next week's meeting a discussion of the canonical use cases and scope limitations for the V1 ToIP stack.
ACTION: Drummond Reedto add chained root of trust topic to the agenda for next week's calls.
ACTION: Drummond Reed to add spanning layer discussion to the agenda for next week's calls.