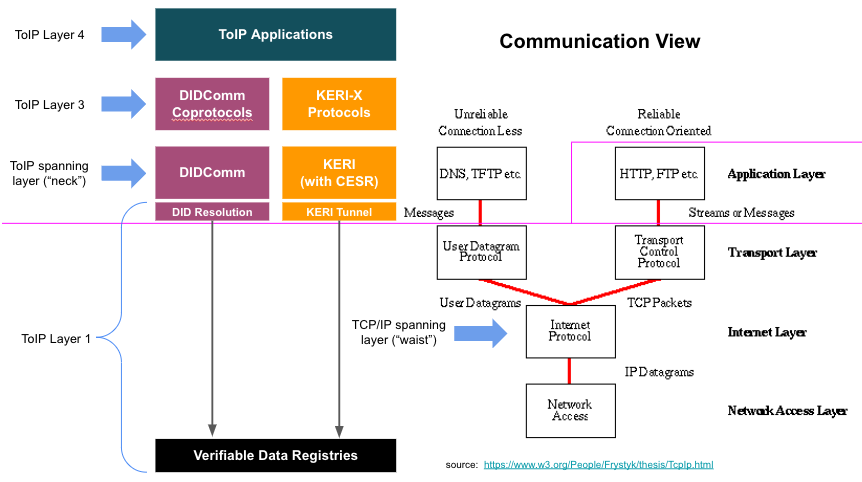
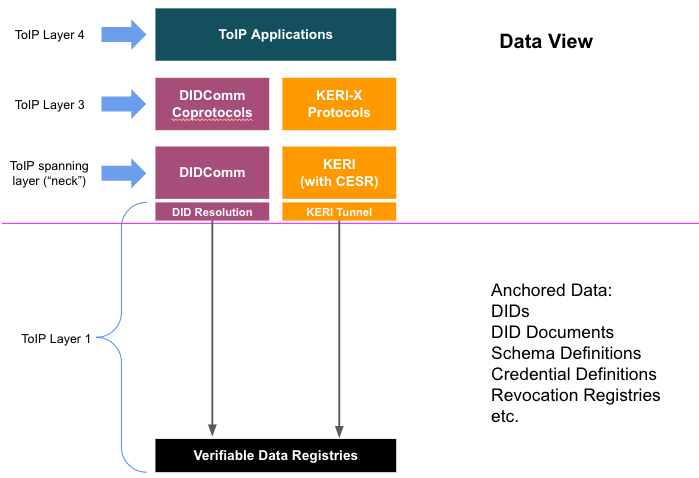
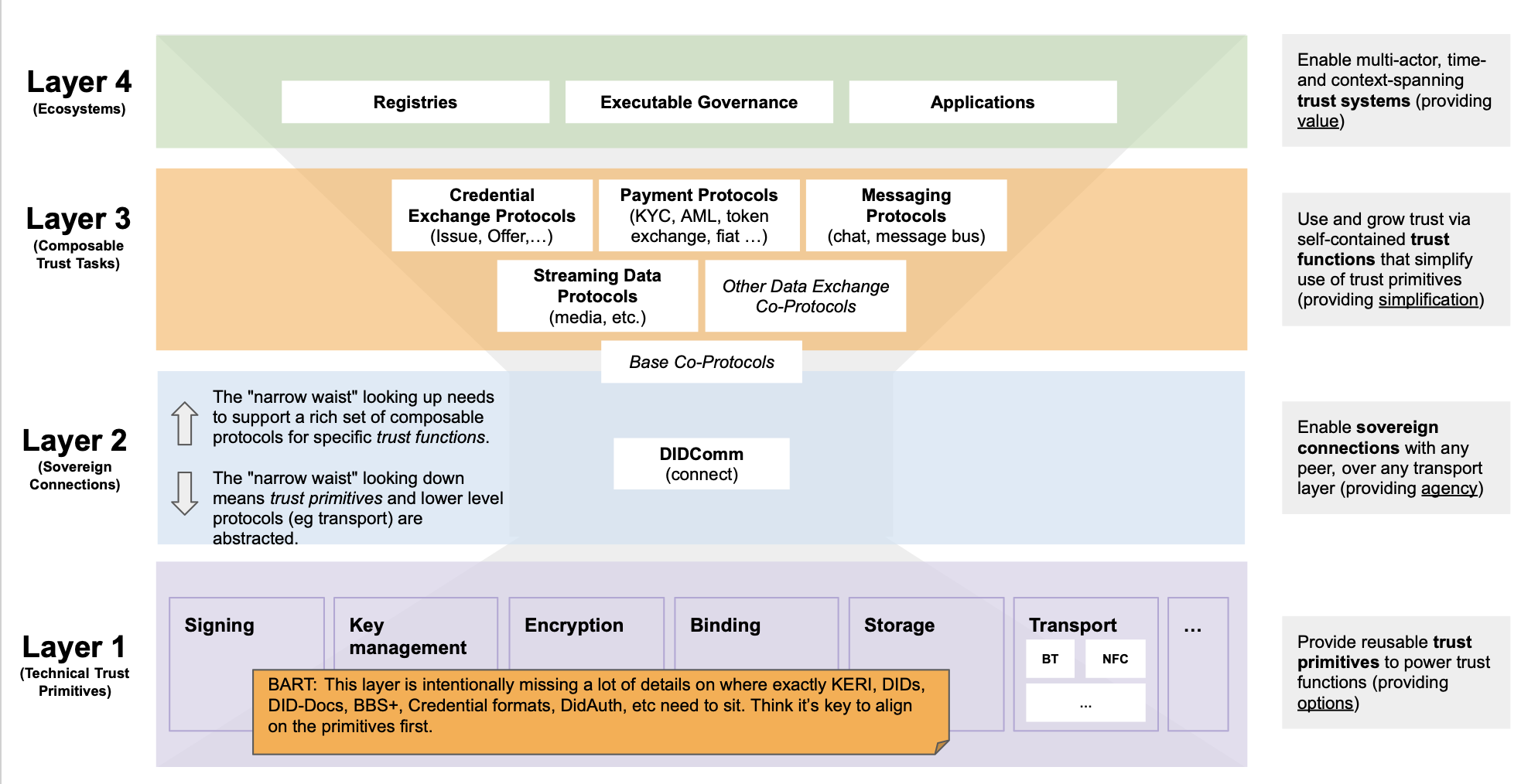
We discussed the proposed consolidated technical protocol stack diagrams:
Discussion notes:
- Wenjing Chu offered to write a "reference view"
- ACTION: Wenjing Chu to prepare a "reference view" diagram of the ToIP stack to present next week
- Daniel Bachenheimer pointed out that the term "key management" really only applies to Layer 2 because that is where the digital wallets live that handle key generation and local storage and the digital agents that then call the Layer 1 interface protocols (e.g., DID resolution or KERI tunnels) to register key material with Layer 1 verifiable data registries (VDRs).
- Antti Kettunen pointed out that Layer 1, in the third view, could start to look like a "trash pile" of different ways to store the cryptographic primitives.
- Drummond Reed explained about the DID URL Resource Parameter Specification.
- This can standardize the interface for Layer 1 to return any necessary cryptographic primitive
- Bart Suichies looks at the layers from a different perspective.
- In the EU there is a discussion about certification of 450K endpoints
- Layer 1 should not be just a storage layer
- Does key management really reside at Layer 2?
- Drummond asked Bart if he wants to create a "view" of the stack
- Wenjing Chu advocated that our job is to define the standard interface to Layer 1 and then let the market decide which implementations will survive in the market
- Daniel Bachenheimer said "If Layer 1 (VDR) is to cover CENTRALIZED schemes as well (e.g., Certification Authorities) then Key Management would fit"
- Darrell O'Donnell agreed with Dan on that point — that the ToIP stack can accommodate the existing PKI solutions
- ACTION: Drummond Reed will add the point about "accommodating legacy approaches" into the narrative of the storyline deck (see below).